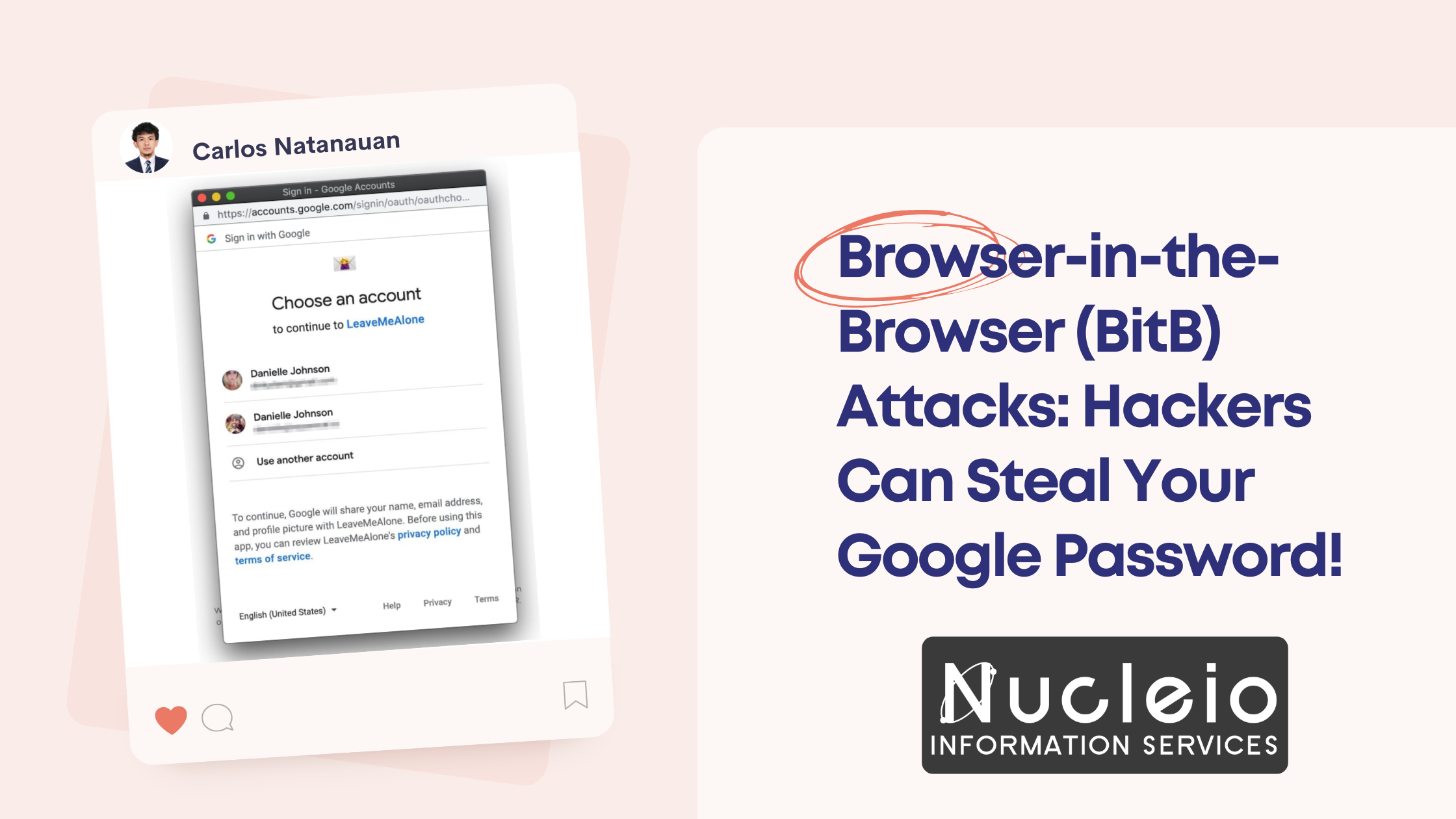
Browser-in-the-Browser (BitB) Attacks: Hackers Can Steal Your Google Password!
Think your Google password is safe? Think again. A sneaky new phishing technique called Browser-in-the-Browser (BitB) attacks can trick even tech-savvy users into giving away their precious login details. In this post, we’ll break down how BitB attacks work and give you a simple tip to protect yourself. Understanding BitB Attacks The Simple Trick That […]
Browser-in-the-Browser (BitB) Attacks: Hackers Can Steal Your Google Password! Read More »