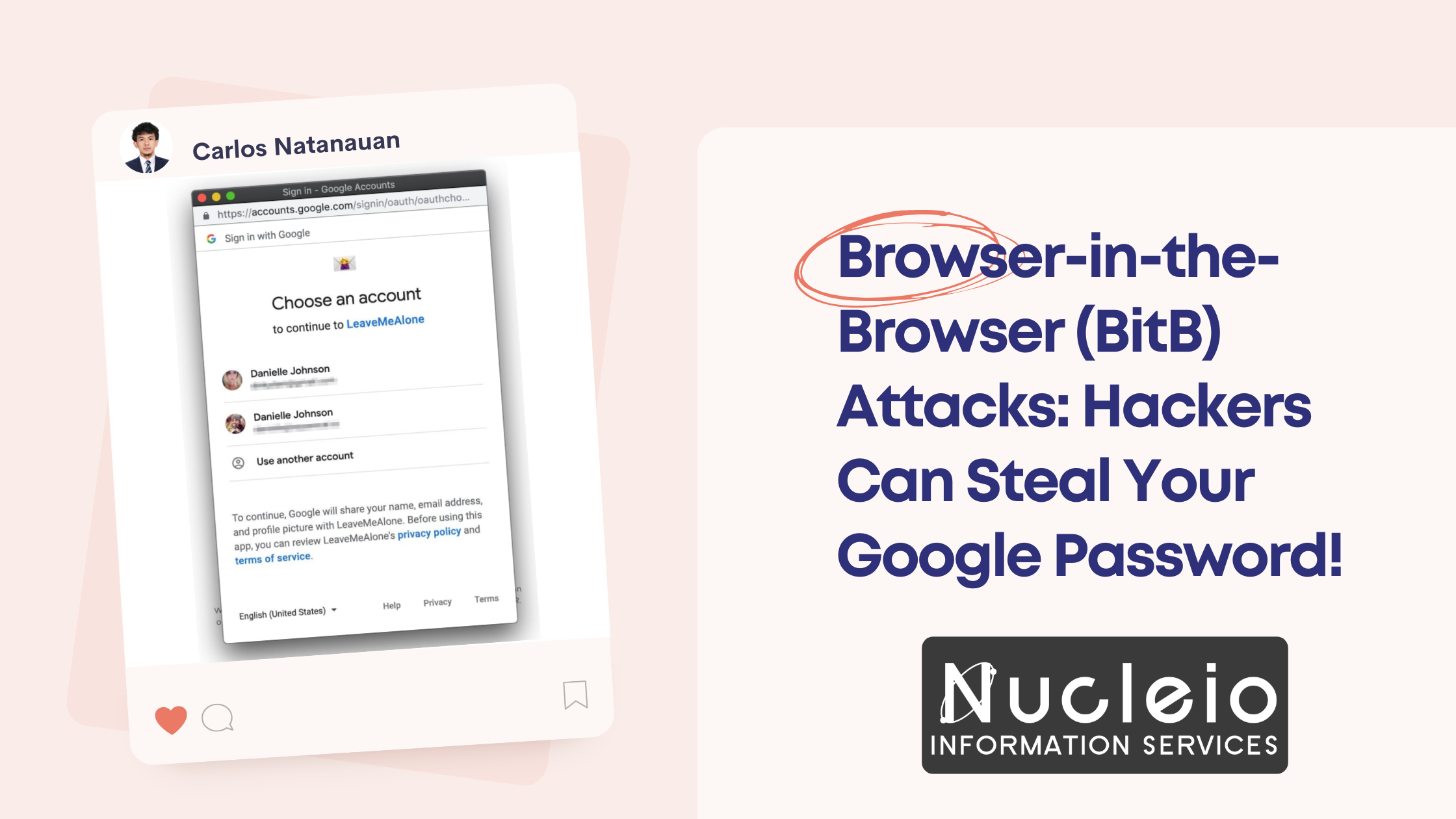
Think your Google password is safe? Think again. A sneaky new phishing technique called Browser-in-the-Browser (BitB) attacks can trick even tech-savvy users into giving away their precious login details. In this post, we’ll break down how BitB attacks work and give you a simple tip to protect yourself.
Understanding BitB Attacks
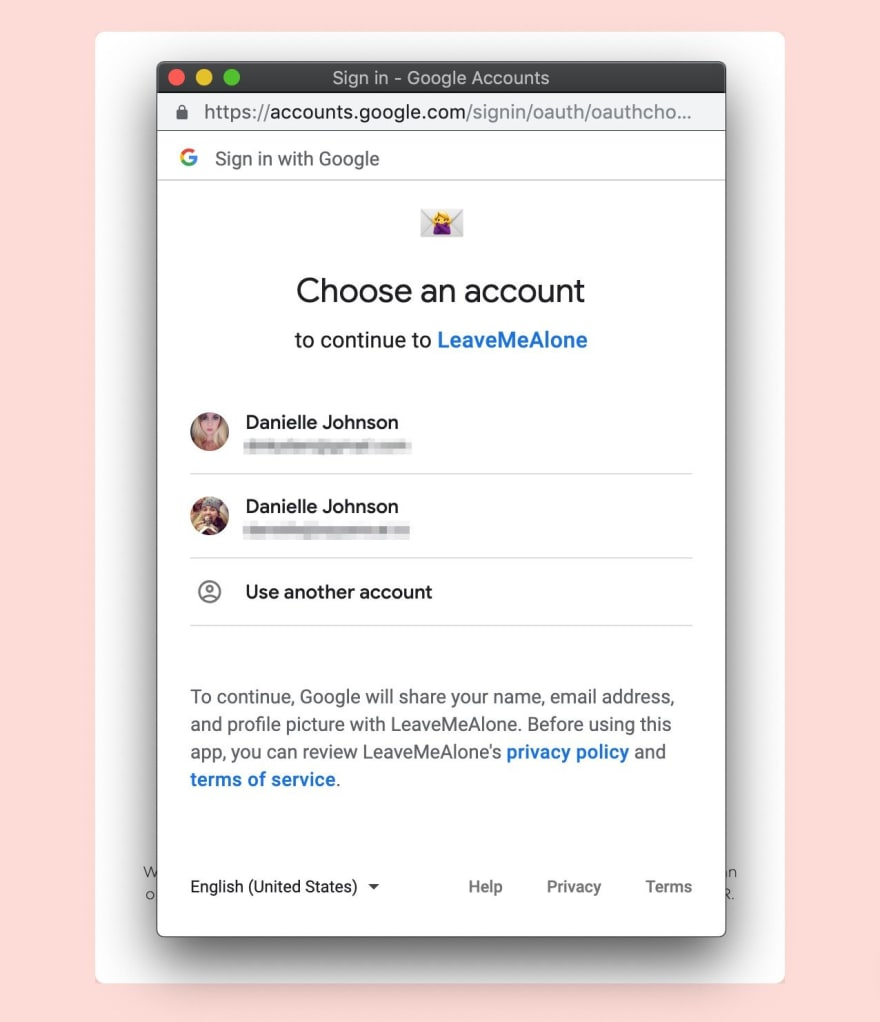
- The Fake Login: BitB attacks start with a malicious website. The catch? This website might look like something you trust – a news site, social media platform, or even a shopping site. When you try to log in, instead of the real login page, the attackers simulate a fake “browser window” within the actual browser.
- The Convincing Look: These fake browser windows are incredibly detailed. They might have a realistic address bar (showing something like [invalid URL removed]), the Google logo, and all the visual cues you expect.
- The Stolen Credentials: Unsuspecting users happily type in their usernames and passwords, not realizing they’re giving them directly to hackers.
The Simple Trick That Can Save You: Dragging Your Windows
Here’s the key to foiling a BitB attack: try dragging the login window outside the boundary of your main browser window. Here’s why:
- Fake Windows are Static: The attackers can’t make their fake window interact with the real browser environment. It’ll stay stuck within the website’s limits.
- Real Windows Move: Authentic Google (or any other service) login windows are separate and can be dragged around freely.
Additional Protection Tips
- Be Suspicious of Pop-ups: While some sites use legitimate pop-up logins, be hyper-vigilant with anything that looks out of place.
- Check the URL (Address Bar): Before entering any info, carefully examine the address in the address bar. Is it the exact website you were expecting?
- Bookmark Frequently Used Login Pages: Avoid clicking login links on other sites, go directly to your bookmarked page instead.
Conclusion Browser-in-the-Browser attacks are a dangerous reminder that phishing scams are getting more sophisticated. By staying alert, checking for draggable windows, and following