The landscape of cybersecurity trends is evolving at an unprecedented pace, driven by the relentless expansion of digital connectivity and the soaring volume of data generated and transmitted every second. As our world embraces IoT, cloud computing, and 5G networks, safeguarding sensitive information is more critical than ever. This year, cybersecurity experts face a multitude of new challenges, requiring innovative solutions to strengthen defenses against evolving cyber threats. Ransomware and AI-driven cyber-attacks are escalating, with adversaries growing more cunning, posing significant risks to individuals, businesses, and governments. In this dynamic environment, staying ahead of cybersecurity trends is crucial for safeguarding data and preventing breaches. This sets the stage for exploring the key trends shaping cybersecurity. It highlights the importance of adopting strong strategies to combat evolving cyber threats in our increasingly connected world.
AI-Powered Cyber Defense
The integration of artificial intelligence (AI) and machine learning algorithms has revolutionized cybersecurity practices. In 2024, organizations are leveraging AI to detect and respond to cyber threats in real-time. Predictive analytics and anomaly detection help identify suspicious activities before they escalate into full-fledged attacks. Moreover, by harnessing the power of AI, businesses can enhance their security posture and mitigate risks effectively.
Quantum-Safe Cryptography
With the advent of quantum computing on the horizon, traditional cryptographic methods are facing unprecedented challenges. Quantum computers have the potential to break existing encryption algorithms, posing a significant threat to data security. In response, the adoption of quantum-safe cryptography is gaining momentum. Additionally, these cryptographic techniques are designed to withstand quantum attacks, ensuring the confidentiality and integrity of sensitive information in the quantum era.
Zero Trust Architecture
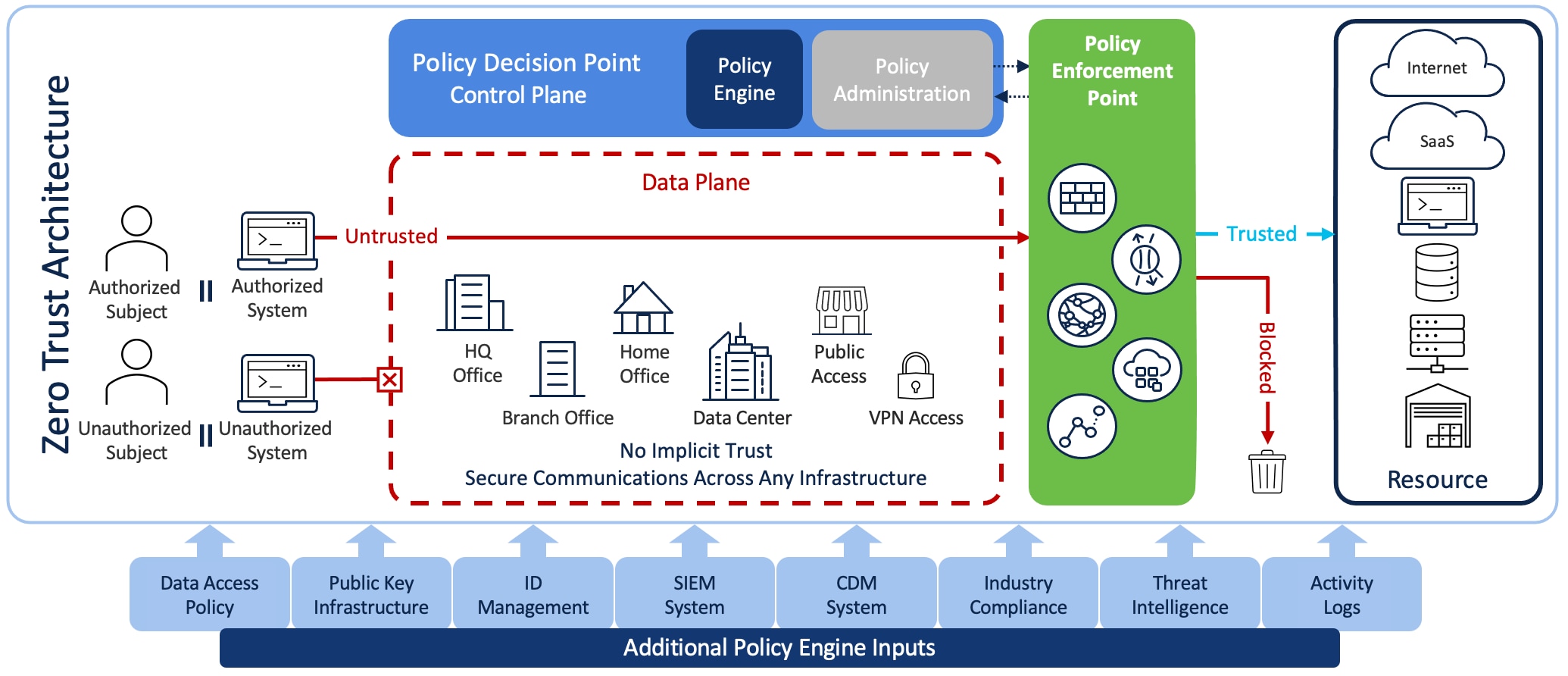
In today’s dynamic threat landscape, the traditional perimeter-based security model is no longer sufficient. Zero Trust Architecture (ZTA) advocates for a paradigm shift towards a more proactive approach to cybersecurity. Therefore, by assuming that no entity, whether inside or outside the network, can be trusted by default, ZTA emphasizes continuous verification of identities and strict access controls. This model helps organizations mitigate insider threats, prevent lateral movement, and protect critical assets effectively.
Cybersecurity Automation
As cyber threats become more sophisticated and prevalent, automation plays a crucial role in enhancing the efficiency of cybersecurity operations. In 2024, security orchestration and automation platforms (SOAPs) are empowering organizations to automate routine tasks, such as threat detection, containment, and remediation. Furthermore, by automating these processes, cybersecurity teams can respond to incidents promptly, reduce human error, and allocate resources more effectively to address emerging threats.
Supply Chain Security

Supply chain attacks have emerged as a significant concern for organizations across various industries. In 2024, businesses are increasingly focusing on securing their supply chains to prevent potential vulnerabilities. Enhanced due diligence, security assessments, and vendor risk management practices are essential to mitigate the risks associated with third-party suppliers and service providers. By strengthening supply chain security measures, organizations can minimize the impact of supply chain attacks and ensure the integrity of their operations.
That is all! Cybersecurity remains a top priority for organizations and individuals alike in 2024. By staying informed about emerging threats and adopting proactive security measures, we can effectively protect our data and privacy in an increasingly connected world. Embracing AI-powered cyber defense, quantum-safe cryptography, Zero Trust Architecture, cybersecurity automation, and supply chain security can help us stay ahead of evolving threats and safeguard our digital assets effectively. Stay vigilant, stay secure!

