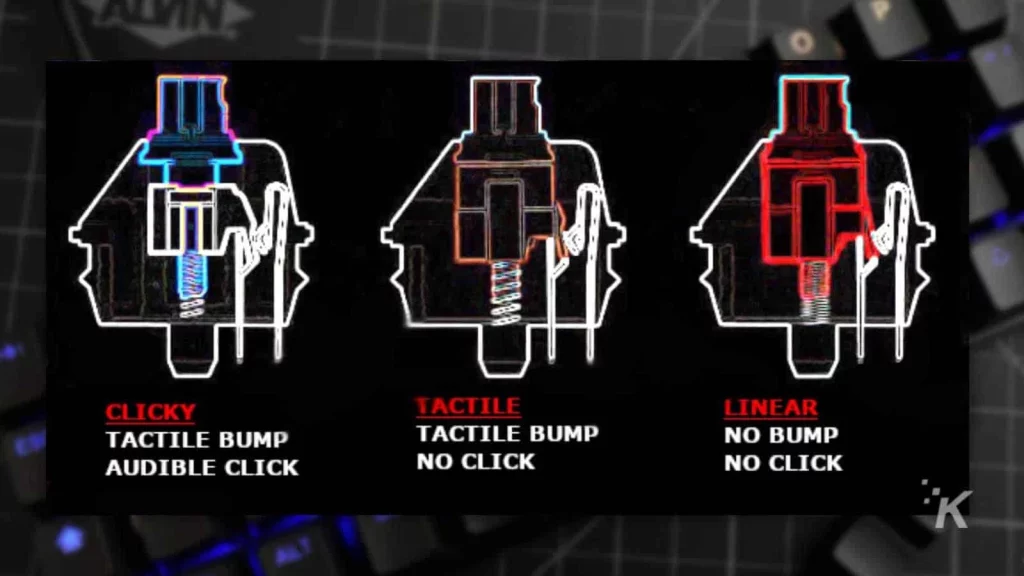
How to Choose the Right Laptop in 2024?
Choosing the Right Laptop in 2024 Feeling lost in the vast ocean of laptops? Don’t worry, we’ve got your back! This guide equips you with the knowledge to confidently choose the right laptop for your needs, budget, and lifestyle. Let’s navigate the laptop landscape and explore some must-have apps to supercharge your productivity. Part 1: […]
How to Choose the Right Laptop in 2024? Read More »