A man in the middle (MITM) attack occurs when a perpetrator enters himself into a communication between a user and an application, either to listen in or to mimic one of the parties, making it look as though a regular information exchange is taking place.
This form of assault is comparable to the game of telephone, in which one person’s remarks are passed from one person to the next until they have altered by the time they reach the last person. A man-in-the-middle assault occurs when a third party intervenes in a communication without the knowledge of the two genuine parties, in order to get sensitive information or inflict other harm.
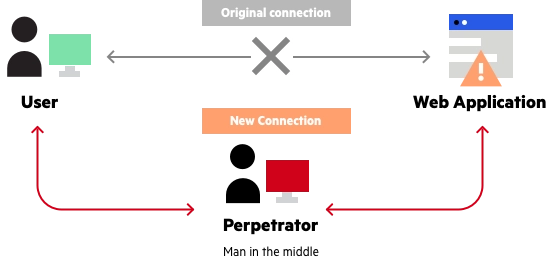
An attack’s purpose is to steal personal data such as login passwords, account information, and credit card numbers. Users of banking apps, SaaS enterprises, e-commerce sites, and other websites that require signing in are typical targets. Identity theft, unapproved financial transfers, and unauthorized password changes might all be possible with information gathered during an attack.
Man in the middle attack prevention
Blocking MITM attacks requires several practical steps on the part of users, as well as a combination of encryption and verification methods for applications.
For users, this means:
- Avoiding WiFi connections that aren’t password protected.
- Paying attention to browser notifications reporting a website as being unsecured.
- Immediately logging out of a secure application when it’s not in use.
- Not using public networks (e.g., coffee shops, hotels) when conducting sensitive transactions.
References:
https://www.imperva.com/learn/application-security/man-in-the-middle-attack-mitm/
https://www.veracode.com/security/man-middle-attack
